Google Chat Security And Compliance Overview

Google Chat has fast become one of the go-to applications for small and large businesses alike.
As any digital architect or CIO knows, choosing and pursuing the adoption of collaboration tools comes down to a number of things. But none are more important than security and compliance.
In this blog post, we walk through how Google Chat keeps your workplace secure and compliant.
Let’s start with some key features.
Key features of Google Chat security
As part of Google Workspace, the business suite of Google apps and services, Google Chat benefits from the same security protocols applied to the rest of the Google infrastructure.
Over a decade ago, Google implemented its BeyondCorp framework—a zero-trust approach to protecting user credentials—and BeyondProd—its internal method for zero-trust production.
Administrators of Google Workspace can use Cloud Identity features to manage security keys, multi-factor authentication, and user access from a single place.
1 - Identity and device management
Google offers endpoint management of your users’ devices with different levels of permissions and controls, depending on the level of security you need.
All apps come with basic mobile security against hijacking. However, if organizations want enhanced security and increased control they can implement advanced security and app management protocols that require users to install a management app on their devices.
This allows admins to control the organization’s data, require stronger passwords, and wipe devices remotely in case they’re stolen or lost.
SAML-based single sign-on
Security assertion markup language (SAML) is an XML standard that allows secure web applications to exchange user authentication and authorization data.
Google supports SAML-based SSO and companies can use a number of open source and commercial identity provider solutions to implement SSO with Google.
If you want your users to access Google services with a desktop client, like Outlook, you still need to provide users with passwords and then sync those passwords with your internal user database using Admin SDK’s Directory API.
Session length
The default web session length for Google services is 14 days. But the session for delegated and super admins is one hour and this can’t be changed in the Google Admin console.
In order to update the session length for your users, you’d need to log in to Google Admin and then:
- Go to Security
- Click on Access and data control
- Then click on Google Session Control

Then, on the left-hand side, you can select if you want to change the settings for the whole organization or sub-accounts and departments.
2-step verification
Google gives administrators the option to enforce 2-step verification and choose between several types of secondary verifications.
Some of the options they can choose from are:
- Security keys
- Google prompt
- Google authenticator and other verification code generators
- Backup codes
- Text message or phone call
In order to deploy 2-step verification, administrators need to log in to their Google Admin console and go to Security -> Authentication -> 2-Step Verification.
Admins can either apply these rules to all users or select child organizations or a custom configuration group.

User and group provisioning via SCIM
The system for cross-domain identity management (SCIM) is an open standard for automating the exchange of user identity information between identity domains or IT systems.
Customers of their Business Starter and Frontline subscription plans can configure up to three apps for automated remote provisioning while those on Business Standard, Plus, or Enterprise plans can configure an unlimited number of apps.
To set this up, users first need to set up SSO and then select their app for which they want to enable remote provisioning.
Domain claiming
Google Workspace allows companies to claim their domains to ensure nobody else can log in to Google Workspace using their company domain.
In order to do this, administrators will need to copy a verification code from the Google Workspace setup tool and paste it into the DNS records for their domain name.
2 - Mobile device management
As an administrator, you can decide the level of control you want to maintain across your users’ devices.
As well as the default basic device management capabilities, you can apply advanced settings that support the implementation of specific security policies, bulk enrollment for company-owned desktop devices, and remote device wipe.
To see the full list of differences between the basic and advanced management features, click here.
Here’s a list of supported mobile and desktop devices for Google endpoint management.
Enterprise mobility management (EMM)
EMM allows you to define when and where your Google applications are available, including Google Chat.
Administrators can either use Google’s endpoint management or they can use a third-party EMM provider. The Enterprise Solutions Directory offers a list of third-party EMM providers.
Those who have the Android Enterprise Recommended checkmark meet the advanced set of enterprise requirements.
Secondary authentication
Google recommends administrators and users with access to sensitive data to have 2-step verification always enabled. While you can choose from a set of different verification methods, SMS messages are discouraged as they rely on external networks that can be intercepted.
Block message copy and file download
Administrators can use S/MIME encryption for outgoing messages to enforce compliance and routing rules.
They can use this to filter their content for specific text. For example, where confidential content is shared or set a defined list of IP addresses. Messages outside of this range will be quarantined.
When it comes to Google Chat, super admin users can set file sharing rules via the Google Admin console following these steps:
- Go to Menu
- Click on Apps
- Google Workspace
- Google Chat
- Chat File Sharing

Here, if you’d like to apply your rules to the whole organization, select the top organizational unit. Otherwise, select a child organization or a configuration group.
You can also define the types of files people can share in internal or external communication and choose between all files, images only, or no files.
Admins also have the option to manage the chat history by switching it On or Off in the Google Admin console.
Block jailbroken or rooted devices
Google allows administrators to block jailbroken or rooted devices both for Android and iOS via their advanced mobile management as well as approve devices before they can be put in use.
In order to block data syncing with such devices, administrators need to check the Block compromised Android devices or Block jailbroken iOS devices box.

Minimum app version
Google Chat’s standalone app is built using Progressive Web App (PWA) technology which means the app updates automatically provided the users keep their Google Chrome browser up-to-date (version 73 or higher).
The app is supported on Windows, macOS, Chrome OS, and Linux.
3 - Data protection
Enterprise encryption
Google uses end-to-end encryption where data is encrypted both at rest and in transit, both on disk and backup media.
When it comes to at-rest data, conversations, images, videos, links, and uploaded files are encrypted when history is on. This doesn’t apply to conversations when history is off.
Cloud key management (CKM) or bring your own key
Google offers a cloud-hosted, key management service where clients can generate, use, rotate, and destroy AES256, RSA 2048, RSA 3072, RSA 4096, EC P256, and EC P384 cryptographic keys.
They also have the option to store their encryption keys in a third-party key management service outside of the Google infrastructure, using BigQuery or Compute Engine, for added security.
Data loss prevention (DLP)
In order to implement DLP rules for your chats, you’d need to have an Enterprise or Cloud Identity Premium account.
Using DLP, admins can enforce rules that block certain messages and attachments from being sent, warn users from sending them, or logs them for audit. They can also define data sensitivity conditions and enforce data protection rules for the whole organization or specific departments.
Audit logs API
There are two types of audit logs administrators can access:
- Admin activity audit log that shows when someone modified the configuration or metadata of resources
- Data access audit logs that show user-driven API calls to read, modify or create user-provided resource data
When it comes to Google Chat, administrators can make API calls to see when users have uploaded or downloaded an attachment, used emojis, or edited/posted or reported a message, among other things. They’d need to use Activities.list() to retrieve this data.
4 - Information governance
Global retention policies
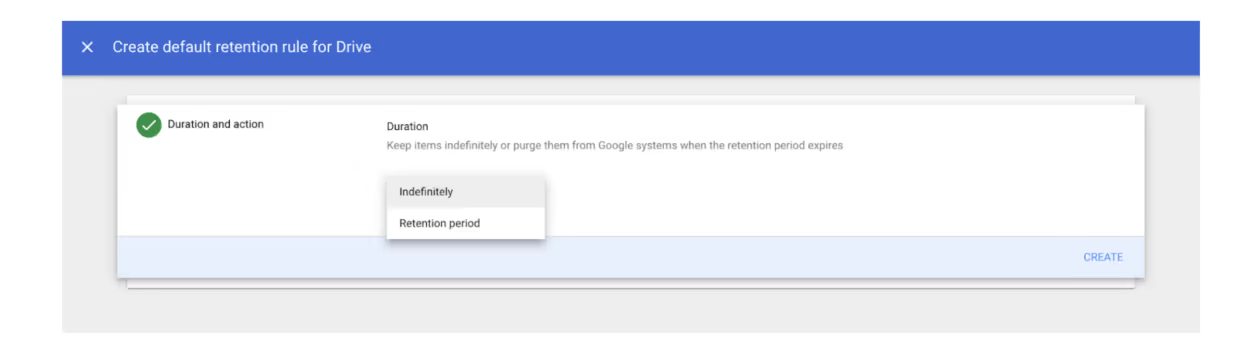
Google Chat’s messages and attachments can be stored for a specific amount of time using Google Vault.
If an administrator wants to set custom rules for their organization, they can do so following these steps:
- Go to vault.google.com
- Click on Retention -> Custom Rules -> Create
- Select Chat-> Continue
- Select either a specific organizational unit or all chat spaces.
- Select either Indefinitely to keep messages permanently or select Retention period and define a range of days between 1 to 36,500
- Click Create
eDiscovery
eDiscovery is available for customers who have Google Workspace Business or Enterprise subscriptions via Google Vault at no additional cost.
That said, once a user account is deleted all the data associated with that account is deleted as well. Google advises customers to suspend rather than delete accounts.
When it comes to Google Chat conversations and attachments, history must be turned on in order for the data to be retained.
Google Chat compliance certifications
Google boasts some of the most well-recognized third-party certifications as proof of its privacy and security practices.
Here’s a list of Google's compliance certificates:
Conclusion
Google Chat, and its entire Workspace suite, is one of the most secure and compliant collaboration tools on the market.
With plenty built-in, and even more available to integrate with, it’s easy to see why so many enterprises are using the Google suite.
Read Next: Google Is Getting Serious About Interoperability & Integration
Get the latest news from Mio in your inbox.






